Introduction to Quantum Computing and Cryptography
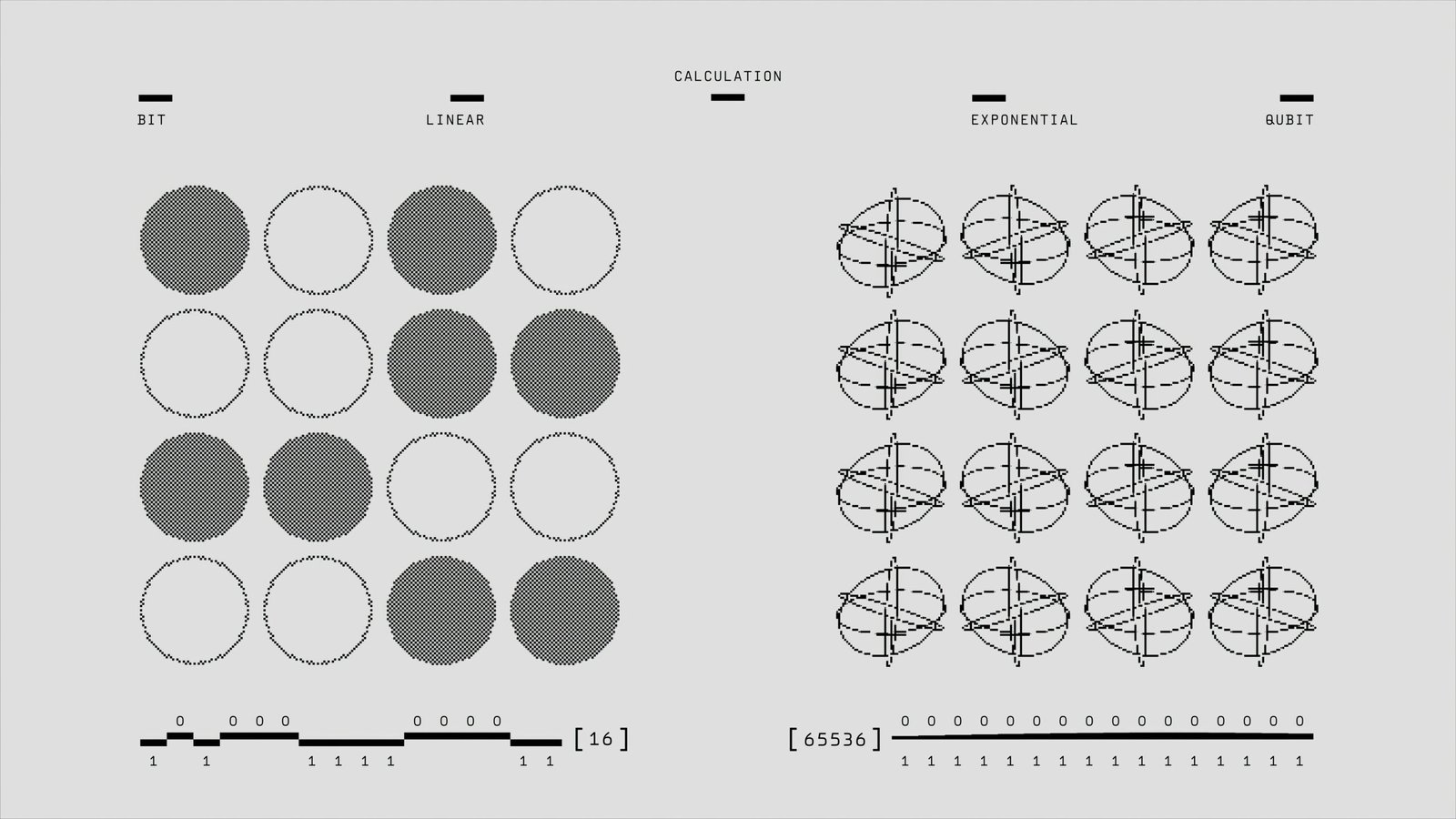
Quantum computing represents a paradigm shift in how computational processes are executed. Unlike classical computers, which use bits as the smallest unit of data, quantum computers utilize qubits. A qubit can exist simultaneously in multiple states, thanks to the principles of superposition. This unique property allows quantum computers to process vast amounts of data more efficiently than classical computers. Another fundamental concept in quantum computing is entanglement, where pairs or groups of qubits become interconnected in such a way that the state of one qubit directly influences the state of another, regardless of the distance between them. These principles enable quantum computers to solve complex problems that are currently beyond the reach of classical computational methods.
Cryptography, on the other hand, is the practice and study of securing information and communications through the use of codes. Its primary goal is to ensure that only intended recipients can access and read the information being transmitted. Cryptography is indispensable in the realm of digital communications, forming the backbone of various security protocols that protect sensitive data from unauthorized access. Techniques such as encryption, decryption, and hashing are employed to safeguard data, ensuring confidentiality, integrity, and authenticity.
The intersection of quantum computing and cryptography introduces both opportunities and challenges. Quantum computers have the potential to break many of the cryptographic systems currently in use, owing to their superior processing capabilities. This has led to the development of quantum-resistant algorithms designed to withstand attacks from quantum computers. The interplay between quantum computing and cryptography is a burgeoning field of research, aimed at securing the future of digital communications in the face of rapid technological advancements.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) stands out as a groundbreaking application of quantum computing in the realm of cryptography. Leveraging the principles of quantum mechanics, QKD provides a method for two parties to share a secret key with a level of security that is theoretically unassailable by classical means. The core strength of QKD lies in fundamental quantum properties such as the no-cloning theorem and the ability to detect any eavesdropping through alterations in quantum states.
At the heart of QKD is the no-cloning theorem, which posits that it is impossible to create an exact copy of an arbitrary unknown quantum state. This intrinsic property ensures that if an eavesdropper attempts to intercept the key, the process of measurement inevitably disturbs the quantum states, flagging the intrusion. This principle is reinforced through protocols like BB84 and E91. The BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984, employs quantum bits (qubits) in four potential states to encode the key, thus revealing any interception through discrepancies in the received data. The E91 protocol, formulated by Artur Ekert in 1991, builds on the concept of quantum entanglement, offering an even more robust mechanism to detect eavesdropping.
Several real-world implementations of QKD have been realized, demonstrating its potential for secure communications. Institutions and corporations have conducted successful experiments, and some systems are already in commercial use. For instance, the SECOQC network in Europe and China’s Micius satellite experiment have illustrated QKD’s feasibility over significant distances and diverse environments.
Despite its promising nature, QKD technology faces tangible challenges. The need for sophisticated and expensive equipment, such as single-photon sources and detectors, limits its widespread adoption. Moreover, the current state of quantum hardware often restricts QKD systems to relatively short distances, though advances in quantum repeaters may eventually overcome this limitation. As research and development in quantum computing progress, the practical applications of QKD are expected to expand, potentially revolutionizing secure communications across various sectors.
Breaking Classical Cryptographic Algorithms
Quantum computing represents a significant paradigm shift in the field of cryptography, particularly in the context of classical cryptographic algorithms. A critical development in this regard is Shor’s algorithm, which dramatically impacts the security of widely used encryption methods such as RSA (Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), and ECC (Elliptic Curve Cryptography). These cryptographic protocols rely heavily on the computational difficulty of factoring large integers and solving discrete logarithm problems—tasks that classical computers find infeasible within a practical timespan.
Shor’s algorithm, however, leverages the unique properties of quantum mechanics to solve these problems exponentially faster than classical counterparts. Specifically, it transforms the intractable problem of factoring large numbers, which forms the backbone of RSA encryption, into a manageable task for a sufficiently powerful quantum computer. Similarly, it efficiently addresses the discrete logarithm problem, undermining the security foundations of DSA and ECC. This quantum computational speedup poses a significant threat to the integrity of many cryptographic protocols currently deemed secure.
Consider RSA encryption, for instance. The security of RSA hinges on the difficulty of decomposing a large composite number into its prime factors. Classical algorithms, such as the General Number Field Sieve, require an impractically long time to factor sufficiently large numbers. Shor’s algorithm, however, accomplishes this task in polynomial time, exposing a critical vulnerability. This vulnerability extends to protocols like ECC, where the discrete logarithm problem underpins the algorithm’s security. With Shor’s algorithm, the quantum computational speedup renders these once-secure systems susceptible to potential quantum attacks.
Theoretical quantum attacks illustrate these vulnerabilities starkly. For example, an attacker with access to a sufficiently advanced quantum computer could decrypt encrypted communications, forge digital signatures, or compromise secure transactions, thus eroding the foundational trust in current cryptographic systems. These examples underscore the urgency for developing quantum-resistant cryptographic algorithms to safeguard information in a post-quantum world.
Post-Quantum Cryptography
As quantum computing continues to advance, the development of cryptographic algorithms resistant to quantum attacks becomes increasingly critical. This emerging field, known as post-quantum or quantum-resistant cryptography, focuses on designing encryption methods that can withstand the computational power of quantum computers. Several approaches are being explored to achieve this goal, each with its unique strengths and challenges.
One of the primary methodologies is lattice-based cryptography. Lattice-based systems rely on the complexity of mathematical lattice problems, which are inherently difficult for both classical and quantum computers to solve efficiently. These algorithms offer a promising avenue for quantum-resistant encryption and have gained substantial attention in recent research efforts.
Another approach is hash-based cryptography. This method leverages cryptographic hash functions to create secure signatures. While hash-based systems are relatively simple and well-understood, they often require large key sizes, which can be a drawback in terms of performance and storage requirements.
Code-based cryptography utilizes error-correcting codes to create secure systems. The most notable example is the McEliece cryptosystem, which has been studied for decades and is resilient against quantum attacks. However, similar to hash-based methods, code-based cryptography can suffer from large key sizes, making it less practical for certain applications.
Lastly, multivariate-quadratic-equations cryptography involves solving systems of multivariate polynomials over finite fields. This approach is known for its efficiency in terms of speed and key size, but it also presents significant challenges in terms of security analysis and implementation complexity.
Ongoing research and standardization efforts, such as those led by the National Institute of Standards and Technology (NIST), aim to develop and implement robust post-quantum cryptographic standards. NIST has initiated a global competition to evaluate and standardize post-quantum algorithms, with a focus on identifying solutions that balance security, performance, and practicality.
Transitioning to post-quantum cryptography involves several challenges and considerations. Performance impacts are a significant concern, as some quantum-resistant algorithms may require more computational power and larger key sizes compared to classical algorithms. Additionally, compatibility issues must be addressed to ensure seamless integration with existing systems and infrastructure.